Democratic movements often talk about transparency. They want all the information about who thinks what and does what, and what was written as a result to be open to outside investigation. The simple reason is that those people, what they say, how they motivate their actions (by morality or the prospect of financial gain), and what is written into law control our lives. Of course there’s a big difference between the law and what gets enforced, which is another area in which maximum transparency is desired.
But one immediately sees that full public disclosure and transparency can’t work in all cases, because the public consists of people desiring to play by the rules, and many that don’t. Opening up every piece of information to the pubic means you also inform those that are looking to evade detection or capture or that are looking for opportunities to commit a crime.
These are your website postboxes. Who has access to them?
Internets non-transparency
The digital sphere, being all encompassing in our lives today, is also struggling with a choice between openness and closedness (apart from the efforts to control access to people, direct them to and make them pay as much as possible for content). The bottom line is : The digital sphere is not transparent. The reason why is that it is not a space, it is a giant warehouse of post boxes with letters in them. Worse still, to access any of the post boxes with letters you need to use messages carried by messengers, and those messengers may not be reliable. So for instance this web page sits in a post box at One.com. When you ask for it by entering www.greencheck.nl in your browser or clicking a link, a message is send to one.com via a number of relay stations, it arrives at one.com, the message is read, it says “Send me the homepage”, the homepage is composed (usually on the fly), and send back via relay stations. Then your browser takes that information (usually incomplete, and to be completed over a few seconds after you see the first content), and renders it, which is like performing music from musical score. If you want to see that score you can right click you mouse and select ‘View source’ or ‘Pagina bron weergeven’.

A web browser
We put post box, relay station, the reading of the message and the rendering in bold because those are all elements that influence the message, the content you will see. They are also very abstract processes that you have limited access or influence over. The way you could survey this system digitally is like driving through dark tunnels with a patrol car, coming across little mailtrucks with boxes of letters, opening them, and then driving on. You can’t see what is in front or behind at all. Every now and then you enter a cavern where roads split and a traffic director is sending some mail trucks into one other tunnel and others another way. But you only have a flashlight and can perhaps ask the traffic director something like “Dit truck so and so pass by here”. The answer may not be true. The digital sphere is super non-transparent.

Vatican mail system
This tunnel based nature of the internet makes it impossible to survey or protect. You can try. You put seals and stamps on the messages, protect the relay caverns, put a tutor next to the browser reading the score, but the nature of the digital sphere is that the process can not observe itself reliably enough to prevent tampering, changing or out right destruction of data.
Encryption
Encryption is the new buzz word, we wrote about block chain technology here, which is a system of serially encrypted data that has the property that once you encrypt data and you include a fingerprint of that encrypted data to encrypt more data, any change (and thus tampering) with data encrypted earlier will be noticable. This is like sending data in little capsules through a pressured water pipe. If someone anywhere along the pipe drills a hole you will see the pressure drop instantly and know not to trust the data. The systems in use today are simply not robust enough, meaning they can be made to stop performing as expected really easily. Encryption does not change that.

A usb connector that secretly allows wifi intrusion
Recently it was discovered that a VPN system (Juniper), had a ‘hole’. This system was used for decades to create private tunnels through the network, so like a separate fenced lane in the tunnel, by which people could view their company servers. All big companies use the technology and where thinking they had the highest form of protection, they did not. The ‘hole’ seemed to be created by the NSA, so the US could have spied on companies around the world for decades. The NSA has a catalog of products and devices to spy on or disturb your communications and data.
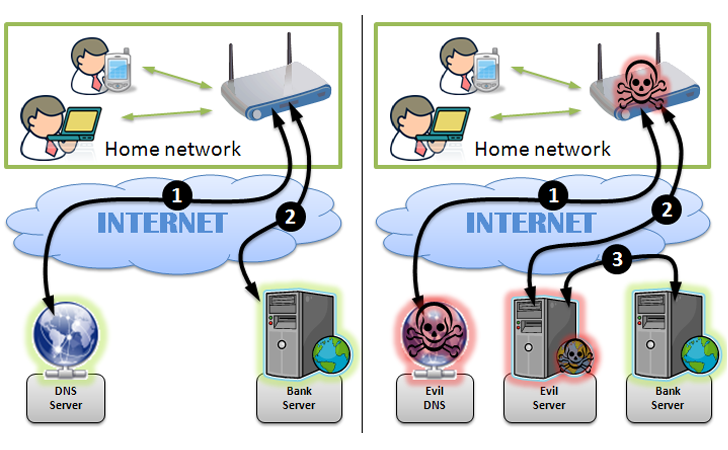
Illustration of how your home wifi network can be hacked. Do you know you see the internet that is out there?
So while the internet tunnel system is super non-transparent, it is transparent to some people that simply drill holes into it and hijack/replace the mail trucks. Even though you may have encrypted your letters it is highly likely that that encryption will contain a flaw or that your private domain will be hacked into (if it is worth it). This means there is yet another way in which those with means can weaken and exploit those without, for instance if it comes to research, the US, with means to spy and introduce ways to siphen off data, can exploit researcg and innovation efforts in other countries. In extrema the interception of messages can allow internet connected people that cooperate to live in separate worlds. This has happened with documents in the European parlaiment, which would be altered as they where transmitted between parties. Imagine the chaos you can create by doing that! The US congress has similar problems where the content of bills (usually hundreds of pages of mostly unrelated laws) has been found to change between the vote and the filing as new law!

Can the internet carry the burden of attacks and it’s own protection, and
will it ever be succesfull?
Economics of security
Recently the SWIFT system was hacked. This is the digital inter bank money transfer system used by banks to reconcile individual transactions (say if dutch tourists shop in Barcelona, that bank will have to get Euro’s from dutch accounts). First a bank was compromized then the SWIFT system using the account of that bank. Like the internet it is very hard to track money flowing through that system, it is not designed to keep track of money or give an overview (and banks like that a lot). The fact is that the battle between those trying to protect valuable digital systems and those that want to attack and exploit them is assymetric. The protector has to do it right all the time, the attacker only once. The protector is more or less on his/her own. The attacker is not and can access a real market for exploits. And it’s not only the digital sphere in which attacks on digital systems take place. This assymetry plus the economic incentive causes the internet to become overburdened and forces it to change constantly, closing vulnerabilities but in the process opening up new ones. Internet can not monitor or secure itself ever, and the market for hacks will mean there is a constant cost to running it that will never pay for real security.
Privacy and Paranoia
On the other side of the spectrum is the constant erosion of privacy. Personal data is spread to unknown parties from unknown sources. Your eye care company may sell the picture of your iris to biometric surveillance firms or governments that want that data to identify you if they want to. Companies like Microsoft aquiring Linkedin gaining valuable information about personal networks of you and me, who do not know who uses that knowledge. Financial data shared between banks and governments, and who else. The tunnel system protects those kinds of cooperation and transfer of data with a granite cloak. The paranoia (about you doubting if you even control your life) this could result in is fair, and people that are not paranoid about it aren’t because they either never thought about it or don’t have the energy. You don’t know if there is not a blacklist for employees, you don’t know if your medical treatment is not done based on your financial reserves. You don’t know if insurance is more expensive for you because the insurer knows about medical history in your family. You don’t know who sees the draft investment rapport. You don’t know if you are browsing the real web, your real bank website, and who knows about your searches (Google clearly does and shares this data).
If someone tells you your data is safe you know there is no way to tell if that is true and it probably isn’t
The internet of things, basically connecting all electrical devices and a lot of non electric ones to the internet, wireless or wired, will only increase the chaos. It will allow sensing in places you may not want it, it will control systems (and be hacked while doing that) you may not want to be vulnerable in that way. Domotica, or devices for computerized control of homes, is aligned with this IoT trend and will make it so your oven can be hacked from Ukraine (or anywhere where there’s an economic incentive), maybe it can be made to do things that are unsafe, maybe hacking can provide entrance to your house or office in ways you had not thought about. Add to that the econmic and energetic and environmental burden of all that silicon and processing. Sure it’s neat to have a tub that knows when you want to take a bath, but there are downsides.
Conclusion
If we assume the internet is not safe and never will be then we have to start thinking where we want it. The economic system does not think about that, it sees an opportunity for change, involving introduction of IoT, internetization of everything. This change will create jobs and keep people bussy, spending fossil fuels, the way the economic rules like it. But reality is that we may be smarter to not go the route the economic opportunities hint at. Criminals show there are many ways to make money, achieve financial gain, but you know you don’t want to engage in those activities. So perhaps some systems are best kept offline, perhaps IoT should be taxed so it only invades parts of our lives where we understand it and can manage it safely.
The transparency principle : The fundamental non-transparent nature of the internet causes it to be fully transparent to unkown parties.
A bigger conclusion following from the above is the need to question large systems. So why do we need data in the EU from the US, why do we need to be served content from Hollywood while we are in the Netherlands. Why do we need to have such large companies and systems that we have such vulnerable infrastructures. Maybe we should not want the companies that need the vulnerable systems to even exist. And what does industrial spying ultimately serve, investments of US banks vs European banks. Why do we compete if once the competition is over everyone drinks coffee at Starbucks. Is localizing food, energy and industrial dependendency chains the ultimate answer to internet vulnerabilites? It sure as hell is cheaper and better for our future to not permeate our existence with a digital retina we intrinsically can’t trust.